Security is a high-stakes game
Security is a high-stakes game that affects the ability to provide quality products and services, both short-term and long-term.
The costly financial and brand reputation impacts of data breaches are making cybersecurity consulting a board-level topic.
As a full-service business and technology consulting company, we’re the right partner to activate your cybersecurity program across an array of project types.
BB Atlantic’s Cybersecurity Consulting Services are designed to help address your most pressing security concerns by guiding you in:
- Establishing enterprise-level governance programs
- Implementing policies that directly address cybersecurity risks
- Driving business continuity through incident response and disaster recovery plans
- Addressing third-party vendor and service provider risks
- Regularly testing infrastructure and business applications
How We Approach Cybersecurity Strategy Development
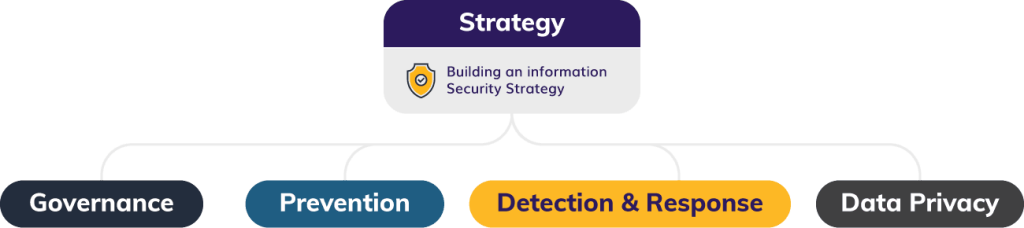
Wondering how to define, organize, and operate a cybersecurity group in your company? Our IT security consultants have a standard approach for strategy development that is aligned with NIST standards and address critical components of any cybersecurity strategy including:
- Governance – processes and policies, IAM management, risk calculation and quantification, compliance management
- Prevention – reducing security exposure, managing vulnerabilities and threats, cloud and application security, security mindset and training
- Detection & Response – penetration testing, ransomware prevention, incidence response, SaaS product platform security
- Data Privacy – applicable laws & frameworks, compliance approach, data privacy program, PII assessment
Our IT Network & Cybersecurity Consulting Services

Virtual CISO
an interim or fractional CISO, or a project-based security team,
having the right team of cybersecurity consultants makes all the difference.
Our Virtual CISO and cyber support models include:
• C Suite Cyber Advisory
• Cyber Resilience & Attack Recovery
• Risk Management & Mitigation
• Compliance Program Management
• M&A Security Due Diligence
• Cyber Liability Insurance Advisory
Audit & Assurance
We help organizations identify and address security gaps, mitigate risks, and ensure compliance with relevant regulations.
Services include:
• Controls Design & Testing
• HITRUST Readiness & Certifications
• SOC Readiness & Reporting
• SOX Testing & IT Audit
Governance Risk & Compliance
Governance establishes policies and procedures, risk is the identification and mitigation of threats to a company’s information assets, and compliance is adherence to relevant laws, regulations, and industry standards.
We’re the right partner for your GRC needs, with services including:
• Risk Calculation & Quantification
• Regulatory Compliance
• Cyber Benchmark Measurement & Development
• Framework Selection, Adoption, and Implementation
• Compliance Management
Penetration Testing
For all types of penetration testing, we provide detailed analysis of threats through thorough evaluations using leading tools.
Our penetration testing capabilities include:
• Network Penetration Testing
• Application Security & Penetration Testing
• Social Engineering Testing
• Specialized Penetration Testing
• Open-Source Intelligence Gathering (OSINT)
• Vulnerability Management
Identity Access Management (IAM)
Our experts are the right partners to help assess your needs, develop an IAM program and roadmap, implement your solution, train your employees, and ultimately monitor your IAM solution.
Project types include:
• Strategy & Policy Definition
• IAM Program Review & Development
• IAM Implementation
• Controls Implementation
• Emerging Technology (BIO, RPA, etc.)
Secure Work Environment
As a Cybersecurity consulting firm with the right team of experts, we consider security paramount and can help with identifying risk, implementing controls, and securing deployments of leading applications.
How we help:
• Cloud Strategy
• Application Security Architecture
• Salesforce, NetSuite, Workday Platform Security
• Microsoft Security
• Microsoft Managed Security
• Emerging Technology (IoT, 5G, etc.)
Cybersecurity Consulting That Addresses Top Threats
Organizations face many cyber threats that severely impact operations, data integrity, and reputation. As bad actors continually evolve their tactics, we advance our own capabilities to help you stay vigilant. Our cybersecurity consulting services fortify defenses across:
Committed to the growth of your company’s startup
59%
of organizations report revenue increases from AI
$67.2
billion invested in AI in the US alone
55%
of organizations use AI in at least one business unit
Our Cybersecurity Support Roles
Cybersecurity Program Manager
Establish the right cybersecurity strategy tailored to your business objectives.
Our experts develop custom roadmaps, implement robust security controls, and manage your entire security program—ensuring your organization stays protected from evolving threats without straining internal resources.
Compliance Manager
Navigate complex regulatory requirements with confidence.
We help manage FFIEC, FISMA, CMMC, SEC Cyber Compliance, and more:
- GRC Management: We integrate security into your business processes while supporting growth objectives.
- PCI Compliance: We guide certification, implement controls, and prepare you for successful audits.
- HIPAA Compliance: We assess your practices, implement controls, and develop programs to protect patient data while enabling efficient operations.
Penetration Test Program Manager
Identify vulnerabilities before attackers exploit them.
We have the right team of experts who are ready to design and oversee comprehensive security testing programs, analyze results to prioritize remediation efforts, and strengthen your defenses against real-world attack scenarios.
Latest News
Read the latest news happening at BB Atlantic and stay updated.
Cybersecurity in the Modern Workplace: Beyond Compliance, Toward Resilience
Cybersecurity is no longer just an IT concern it’s a…
Data Modernization: Unlocking Hidden Value in Legacy Systems
In today’s digital-first economy, data is the most valuable asset…
The Future of AI in Business: Balancing Innovation with Responsibility
Quisque consectetur purus ut suscipit faucibus. Sed at ornare ligula.…


