goals with a structured security
Zero Trust security can keep your business safe from bad actors.
Efforts to enhance employee experience have increased more than ever with the focus on remote work and making it easier to collaborate and improve transactions via digital channels while protecting their data.
These changes have brought to light the importance of establishing a cloud security strategy that keeps their collaboration and transactions in the cloud protected from bad actors without limiting their team’s ability to perform their work.
The Right Approach to GRC
Our GRC services are designed to tackle these issues head-on by helping companies streamline compliance processes to align with various regulatory requirements. We enable organizations to test once and satisfy multiple requirements, significantly reducing redundancy and improving efficiency.
Our proactive approach to GRC advisory and consulting involves integrating risk management activities across the organization, breaking down silos, and providing actionable insights through improved tools and dashboards. We emphasize cross-departmental collaboration, secure stakeholder buy-in and establish strong leadership support for GRC programs.
By partnering with us for GRC services, organizations can transform their cybersecurity governance, risk, and compliance efforts from a complex burden into a strategic asset that enhances overall business performance and resilience.
Our IT Network & Cybersecurity Consulting Services
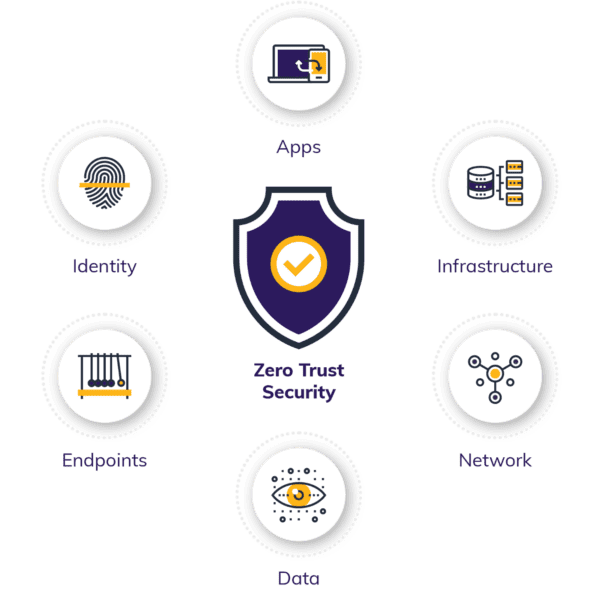
Our Security and Compliance Services
Microsoft 365 Roadmap Strategy & TCOBuild a clear path for deploying and optimizing Microsoft’s suite of productivity tools by aligning your technology investments with business objectives.
Together, we examine your current state and provide a holistic approach to how to best leverage Microsoft as part of your cloud strategy.
Through a series of envisioning workshops, we help identify the actions and considerations you’ll need to have as you plan to expand your footprint in the cloud.
We also review your current Microsoft agreements and provide a Total Cost of Ownership (TCO) and Return-Of-Investment (ROI) evaluation to identify potential cost avoidance.
Foster a secure environment while promoting thriving cloud, collaboration and productivity within your business.
Centric security assessments support your business goals for achieving information and security compliance.
We take a strategic approach by aligning our assessments with the NIST Framework, leveraging the foundation’s benchmark to assess against Microsoft 365-focused CIS Controls.
Enhance your security posture and protect your organization’s data and resources by deploying Microsoft’s cloud-based identity and access management service solutions such as Azure Active Directory to ensure only authorized users have access to critical resources.
By choosing to leverage Azure AD as your central hub for managing user identities, we’ll provide secure access to applications and resources, and ensure strong authentication and security measures across your organization’s IT infrastructure using Single Sign-On (SSO), Multi-factor Authentication (MFA), Conditional Access, Identity Protection, Application Integration, among other use cases.
Reduce the risk of data breaches and other security incidents by leveraging the large range of Microsoft device management solutions like Microsoft Endpoint Manager (MEM), Windows Autopilot, Azure Active Directory, Microsoft Defender for Endpoint and Microsoft Intune.
These solutions help your organizations manage and secure your devices, whether they are PCs, mobile devices, or other endpoints and provide various features and benefits that enhance security, streamline operations, and ensure a consistent user experience across devices.
Protect Your Business and Empower Team Collaboration. Our Experts Can Help You.
Microsoft offers a wealth of robust security solutions that help organizations stay protected when properly configured based on their business requirements. A proper understanding and continuous evaluation of these configurations become important to keep up with the threats that are presented every day.
Our recommendations follow a streamlined approach leveraging robust Microsoft security solutions and more than 25 years of combined experience in delivering technology solutions that ensure the sustainability and continuity needed to grow safely.
The Governance Risk and Compliance Market
2,500
potential target organizations
60
encounter activity associated with known ransomware attackers
20
are successfully compromised
1
falls victim to a successful attack
Our Other Microsoft Related Services
Microsoft 365 ServicesMicrosoft 365 is the most complete and secure cloud productivity and collaboration solution available on the market.
Our Modern Workplace practice is focused on the implementation, adoption, and extension of Microsoft 365 to create a modern, productive and enjoyable workplace that’s aligned to your business goals.
The technology landscape is always evolving and improving. Are you prepared to manage rapid change and demand?
Our Customer Success Management helps your organization manage those rapid changes and demands of using Microsoft 365 products while you focus on core critical business needs.
Without a targeted plan focused on deployment, governance and adoption, you can risk data sprawl, user resistance, and minimal productivity gains.
We take a “business first” approach to using Microsoft Teams for collaboration.
Our Microsoft Certified Professionals help you realize the value of Microsoft Teams not only quickly, but securely and effectively too.
Latest News
Read the latest news happening at BB Atlantic and stay updated.
Cybersecurity in the Modern Workplace: Beyond Compliance, Toward Resilience
Cybersecurity is no longer just an IT concern it’s a…
Data Modernization: Unlocking Hidden Value in Legacy Systems
In today’s digital-first economy, data is the most valuable asset…
The Future of AI in Business: Balancing Innovation with Responsibility
Quisque consectetur purus ut suscipit faucibus. Sed at ornare ligula.…


